IAM Roles in AWS: Secure Access Management for Cloud Resources
A Comprehensive Guide to IAM Roles: Enhancing Security in AWS
Introduction
In today's cloud-centric world, managing access to resources securely is of paramount importance. Amazon Web Services (AWS), the leading cloud service provider, offers a robust access control solution called AWS Identity and Access Management (IAM).
Within IAM, roles play a pivotal role in granting secure permissions to entities accessing AWS resources. In this blog post, we will explore the purpose and significance of roles in AWS, shedding light on how they enhance security, streamline access management, and promote best practices.
Understanding IAM Roles
In AWS, access control is crucial to ensure that resources are securely accessed and utilized. IAM (Identity and Access Management) provides a comprehensive solution for managing access to AWS resources. Within IAM, roles are a fundamental component that sets them apart from other forms of access control, such as users and groups.
IAM roles are entities in AWS that define a set of permissions for making AWS service requests. Unlike users or groups, roles are not assigned to individuals or entities directly but are instead assumed by trusted entities such as AWS services, applications, or users from other AWS accounts. This separation of access control from the individual or entity provides several advantages:
Benefits of using Roles
Least Privilege Access: Roles enable the principle of least privilege, ensuring that entities have only the necessary permissions to perform their intended tasks. By defining fine-grained permissions within roles, you can limit access to specific actions and resources, reducing the risk of accidental or unauthorized access.
Reduced Exposure of Access Credentials: Roles eliminate the need for long-term access keys or credentials. Instead, temporary security tokens are provided when a trusted entity assumes a role. This minimizes the exposure of access credentials, reducing the risk of credential compromise or unauthorized use.
Flexibility and Scalability: Roles are highly flexible and scalable, making them suitable for a wide range of scenarios. They can be easily created, modified, and assigned to different entities without the need for manual credential management. This flexibility simplifies access management and allows for seamless integration with various AWS services and applications.
Cross-Account and Federated Access: Roles facilitate cross-account access, enabling entities from one AWS account to assume roles in another account. This allows for secure collaboration between accounts while maintaining control over resource permissions. Additionally, roles enable federated access, allowing external identities, such as users authenticated by external identity providers, to assume roles and access AWS resources.
By utilizing roles instead of directly assigning permissions to users or groups, you enhance the security posture of your AWS environment. Roles provide a layer of abstraction and separation between users/entities and their associated permissions, promoting a secure and controlled access management framework.
Overall, IAM roles in AWS offer a robust and flexible approach to access control, enabling least privilege access, reducing exposure of access credentials, and facilitating secure collaborations across accounts. They are a fundamental component in establishing a strong security foundation within the AWS ecosystem.
various scenarios where IAM roles are commonly used
IAM Roles for EC2 Instances: When launching EC2 instances, you can assign IAM roles to them. This allows applications running on the instances to securely access AWS services and resources without embedding long-term access keys or credentials within the code or configuration. IAM roles for EC2 instances grant temporary security credentials to the instances, enabling them to make API requests on behalf of the role.
Cross-Account Access: Roles play a crucial role in enabling cross-account access. Suppose you have multiple AWS accounts and want to grant permissions for resources in one account to entities in another account. In that case, you can create a role in the source account and grant permissions to the destination account to assume that role. This allows the entities in the destination account to access resources in the source account securely and with limited privileges. Cross-account access is commonly used in scenarios such as centralized resource management and multi-tenant architectures.
Federated Access: Federated access allows external identities, such as users authenticated by external identity providers (e.g., Active Directory, Facebook, Google), to assume IAM roles and access AWS resources. By integrating with identity federation systems, such as AWS Single Sign-On (SSO) or Security Assertion Markup Language (SAML) providers, you can establish trust between AWS and the external identity provider. This allows users from external systems to assume IAM roles temporarily, enabling them to access AWS resources seamlessly and securely without the need for separate AWS credentials.
Service-to-Service Access: Roles are also utilized to enable secure communication and interaction between AWS services. For example, if you have an AWS Lambda function that needs to access data stored in an S3 bucket, you can assign a role to the Lambda function. The role defines the necessary permissions to read or write data from the bucket. When the Lambda function is invoked, it assumes the assigned role, and AWS automatically provides temporary security credentials. This ensures that the Lambda function can access the S3 bucket securely without compromising long-term access keys or credentials.
IAM Role Configuration
To create and configure IAM roles in AWS, you can follow these steps:
Step 1: - Access the IAM Console:
Sign in to the AWS Management Console and open the IAM service
Step2: - Navigate to Roles:
In the IAM console, click on "Roles" in the sidebar to access the roles management page.
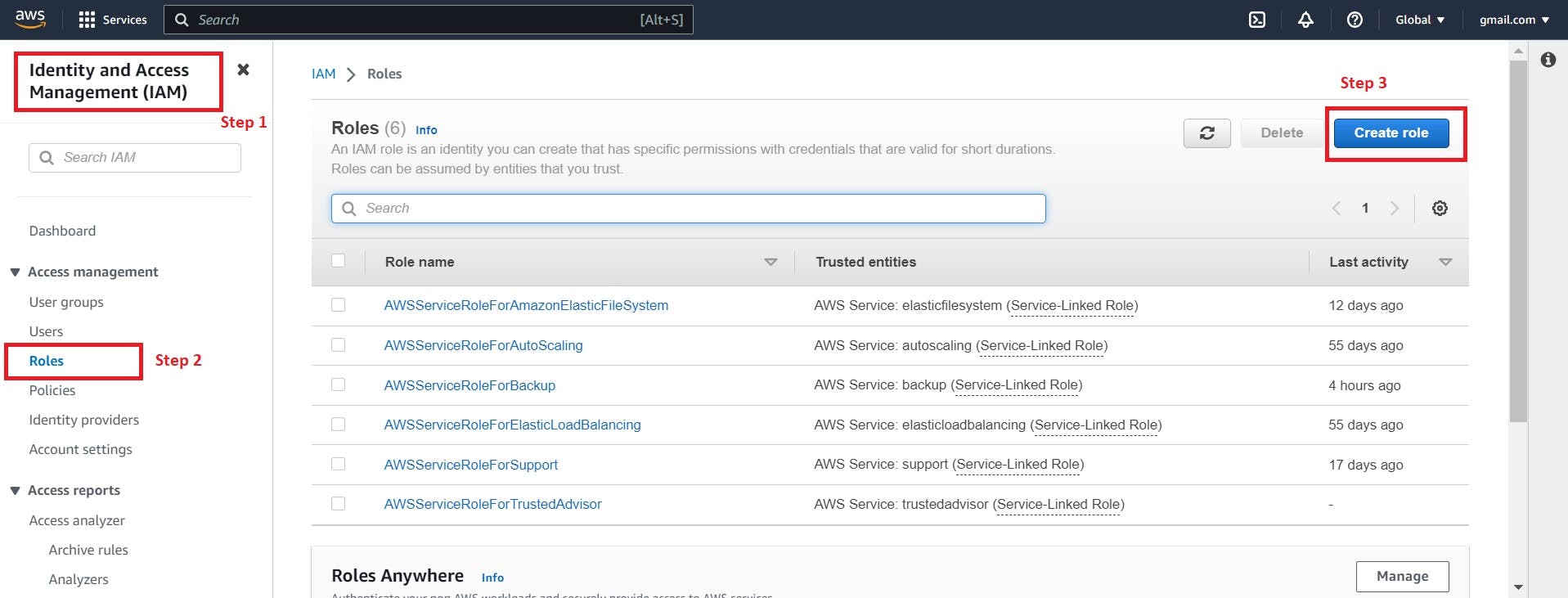
Step 3: - Create a New Role:
Click on the "Create role" button to start creating a new IAM role.
Step 4: - Choose a Use Case:
Select the appropriate use case that matches your requirements. For example, if you want to assign a role to an EC2 instance, choose "EC2" as the use case.
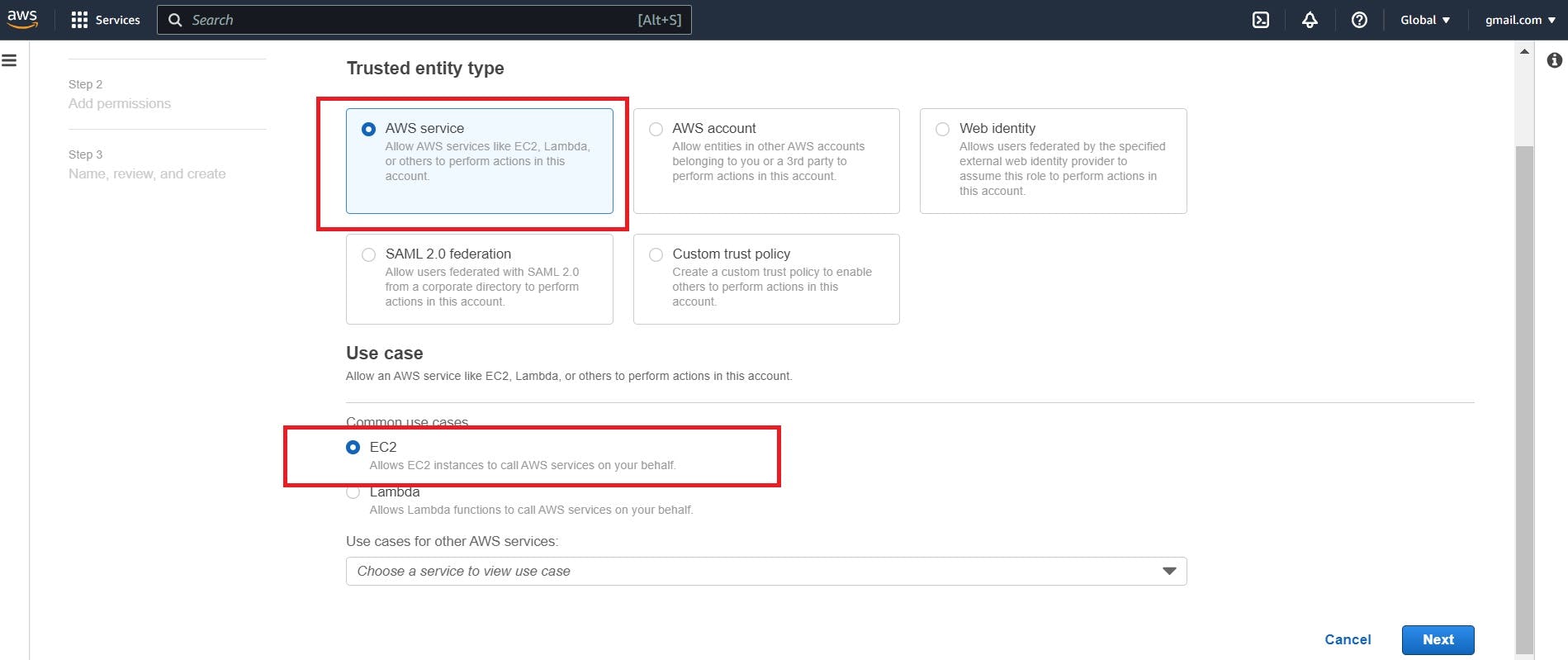
Step 5: - Assign Permissions:
In the next step, you can define the permissions for the role. You have two options:
Attach Policies: Choose existing policies that define a set of permissions and attach them to the role.
Create Policies: Create custom policies specifically tailored for the role.
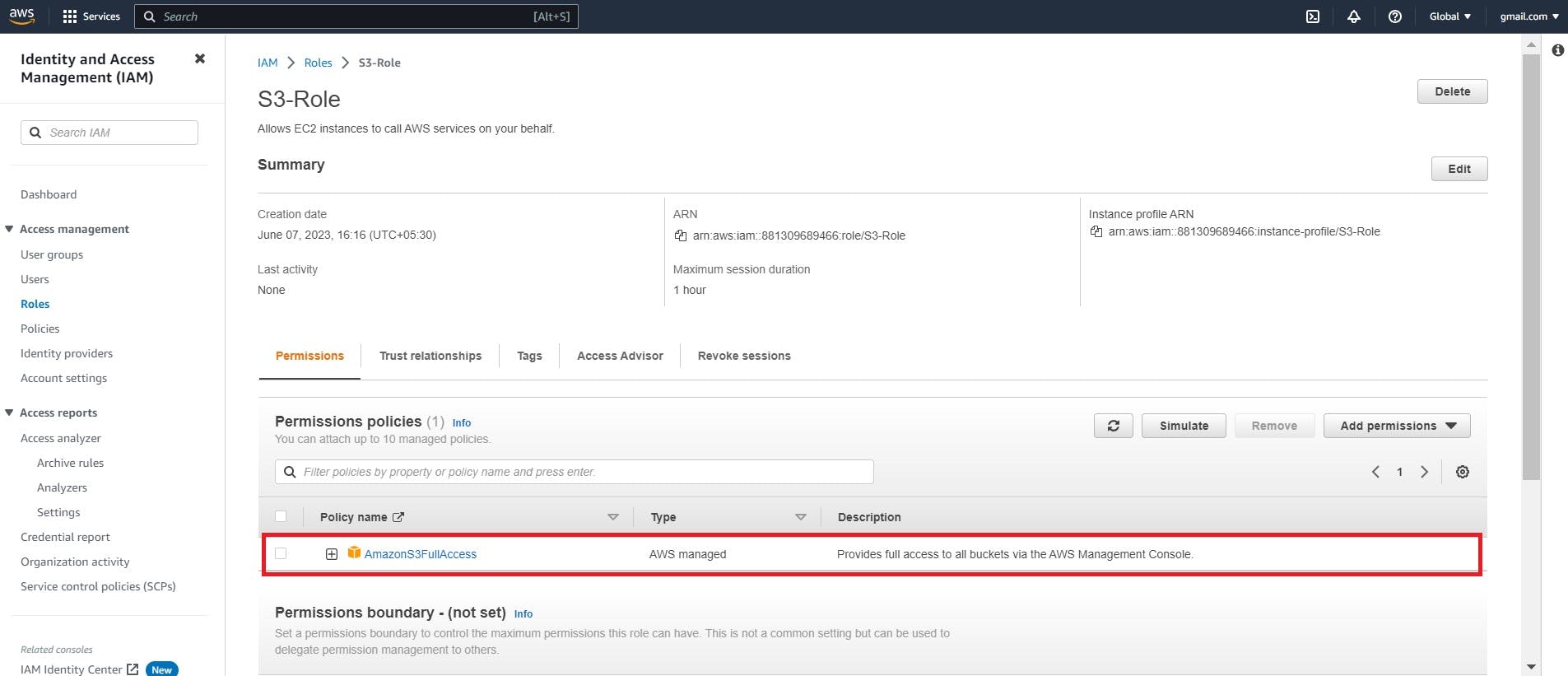
Here I am attaching the existing policy where I will give full access to S3 storage.
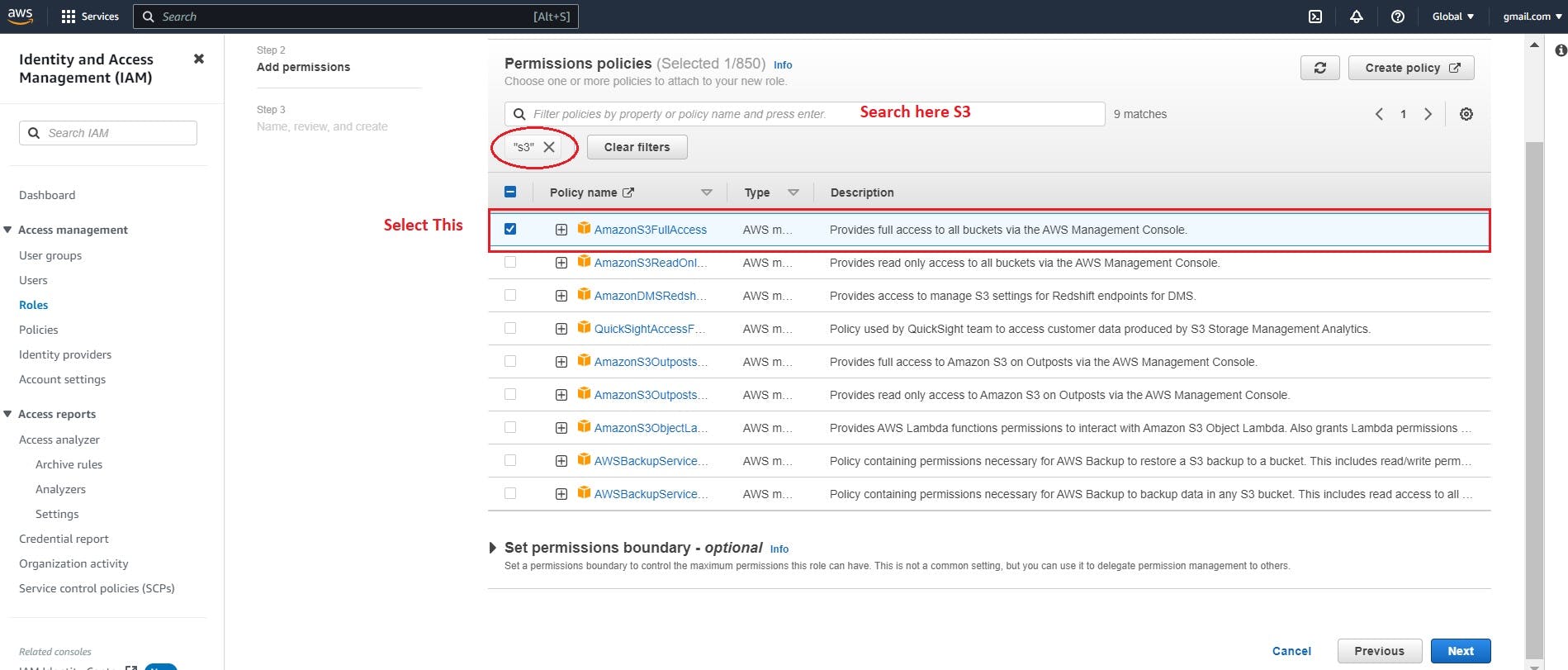
Step 6: - Configure Role Details:
Provide a name for the role and optionally add a description to help identify its purpose.
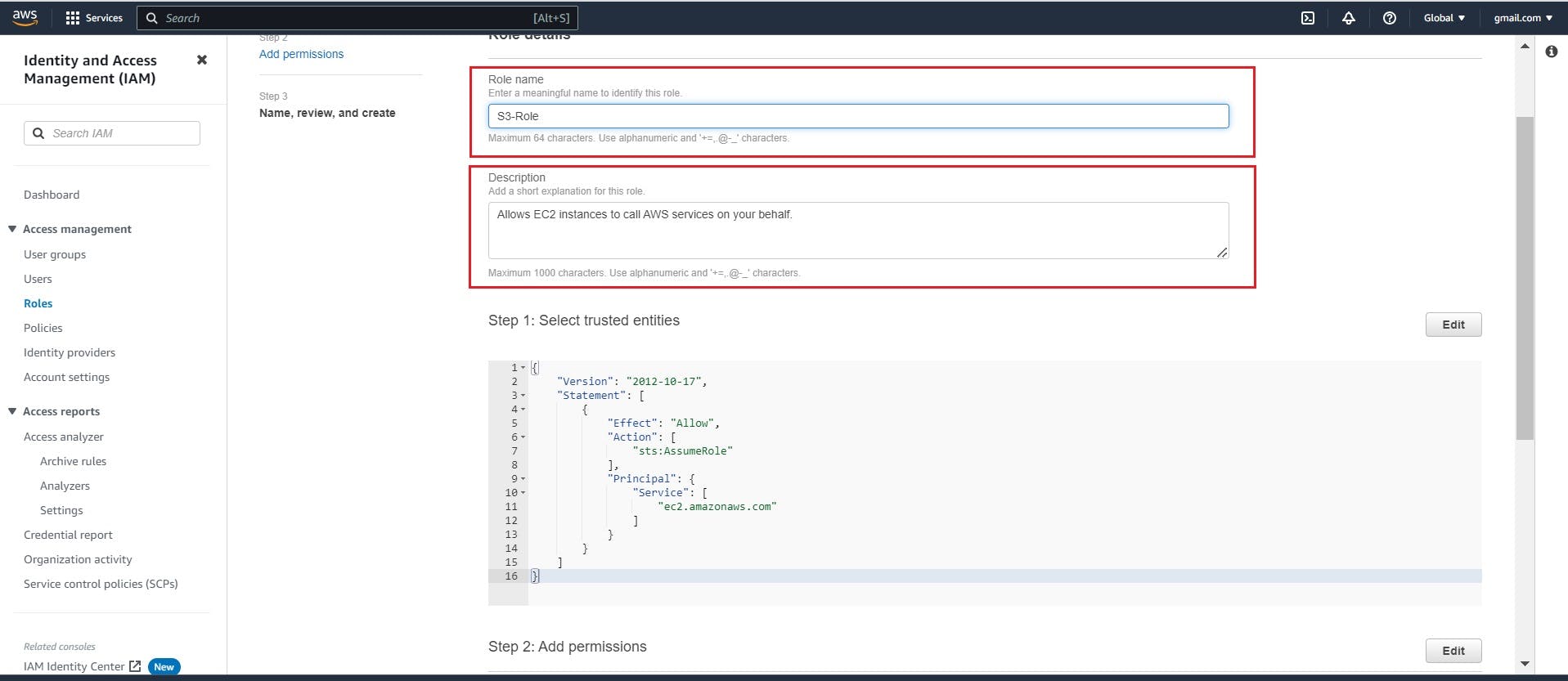
Step 7: - Review and Create:
Review the configuration details and click "Create role" to finalize the role creation process.
Step 8: - Verify
Go to roles and verify the role is created
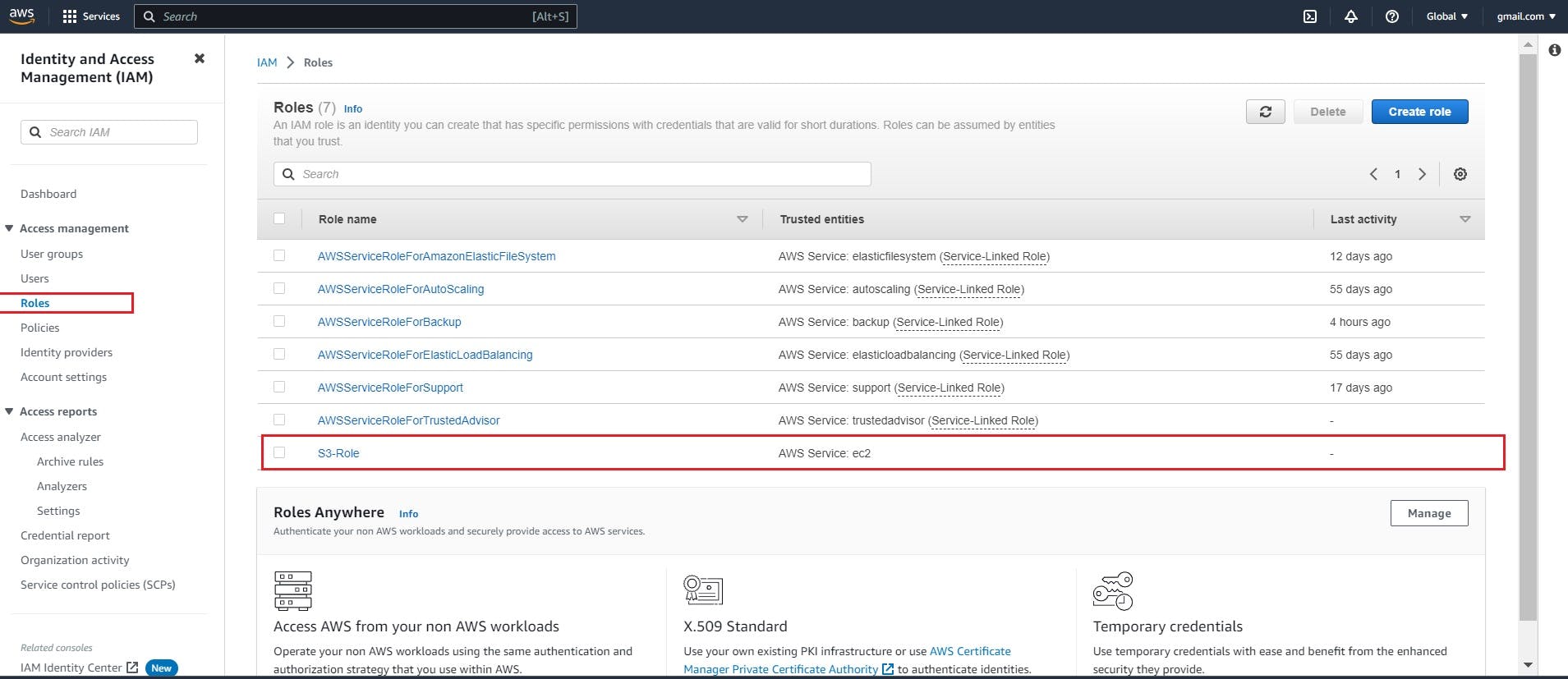
Click on the role which is created and verify whether the policy is attached or not
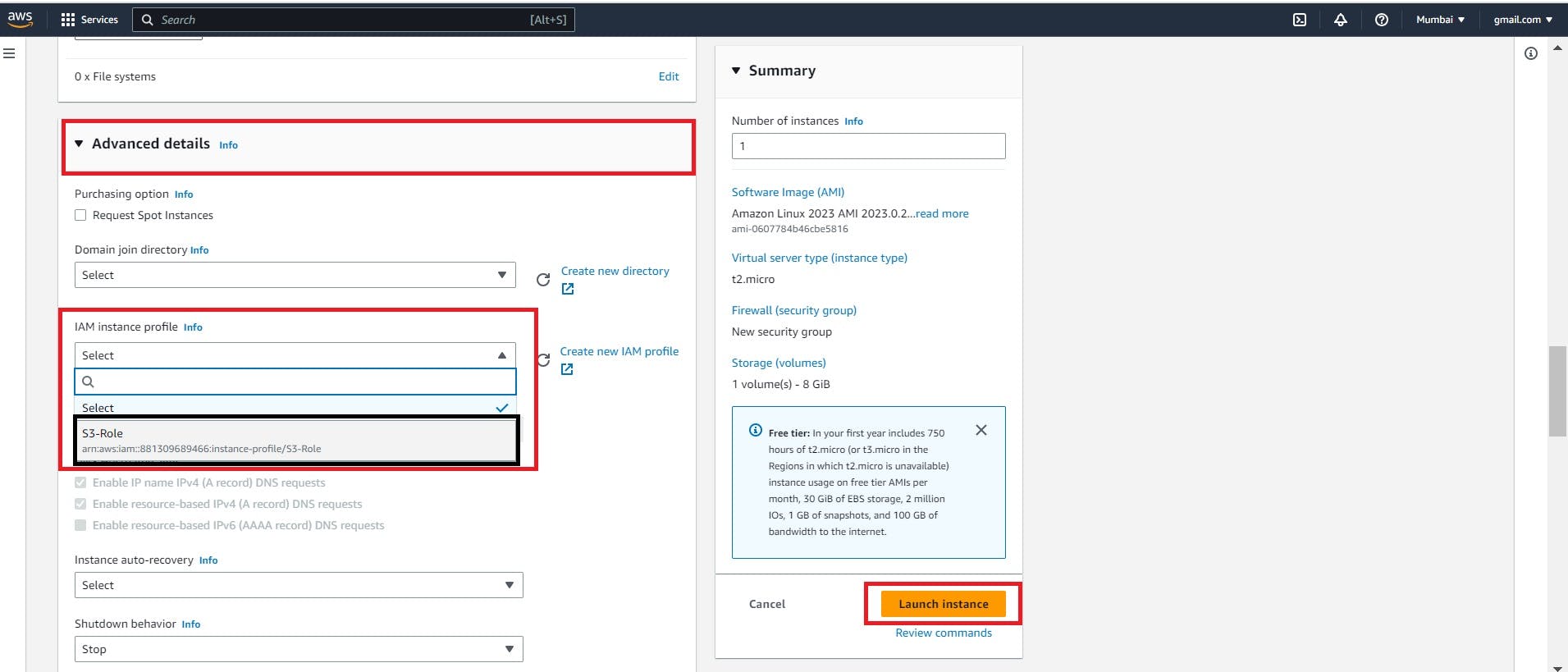
Once, the role is created now we are creating the EC2 instance.
And assign this role to EC2 the instance,
The benefit is we don't require any kind of security credentials to access the services of AWS from the particular AWS account.
Launching EC2 Instance
For more details on how to launch a Linux EC2 instance go through the below blog link
https://hashnode.com/post/cleipnprn000n09l02dvp28xe
While creating a Linux EC2 instance, go Advance details option
Under the IAM instance profile select the role which we created under the IAM service
After Launch the Instance connect it through Putty or MobaX
If you do not know how to connect the Linux EC2 instance please go through my blog, the link is below
https://hashnode.com/post/cles9corf001j3mnv90ay8kau
Accessing S3 service without login
After attaching the role, we do not need any credentials to connect the AWS infrastructure to access the particular service
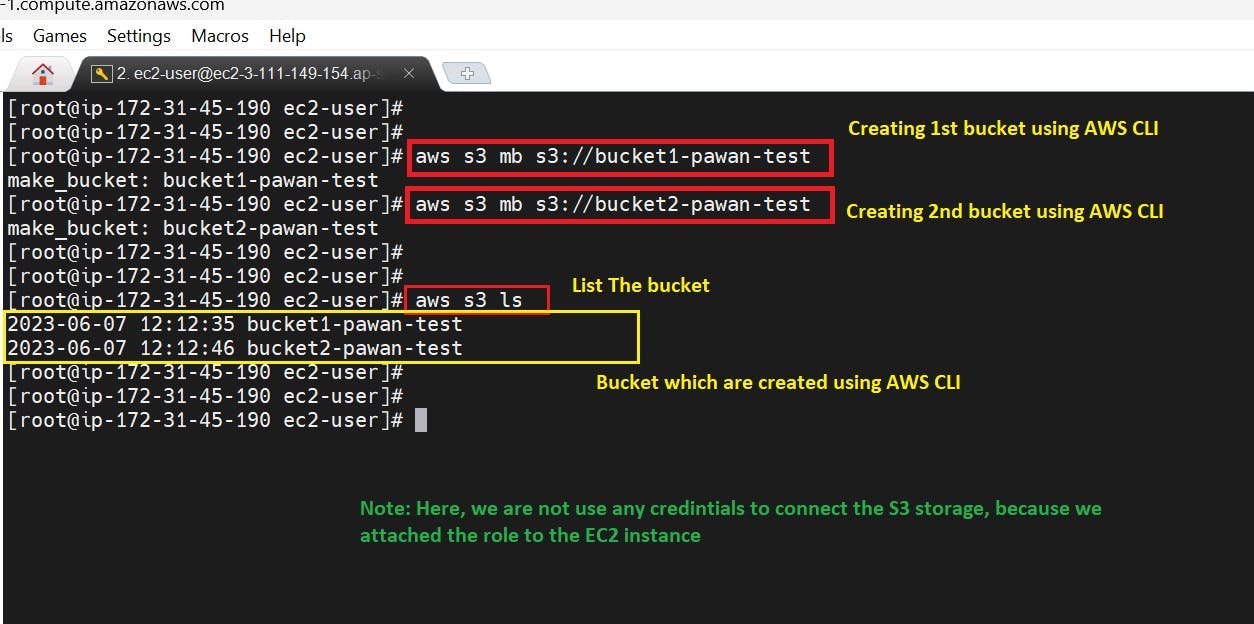
Note: - If we are not attached to the role, we need an Access key id and secrete access key to connect the AWS infrastructure.
Best Practices for Working with IAM Roles
Regularly Reviewing and Updating Role Permissions:
The permissions given to IAM roles should be reviewed and updated regularly. By doing this, roles are guaranteed to have the minimal privileges required to carry out their specified tasks. Examine the permissions given to roles regularly and revoke any unused or excessive privileges. Give only the permissions necessary for particular tasks by following the concept of least privilege.
Implementing Multi-Factor Authentication (MFA) for Role Assumption: For users with IAM role authorization, enable multi-factor authentication (MFA). By requiring an additional authentication factor, such as a physical token or a mobile app, in addition to the user's password, MFA offers an extra layer of security. Even if the user's password is stolen, this helps prevent unauthorized access to roles.
Enforcing Strong Password Policies for IAM Users with Access to Roles:
IAM users who can assume roles should adhere to strong password policies. Strong passwords should be unique, complex, and regularly updated. Enforce password complexity requirements, such as minimum length, a combination of uppercase and lowercase letters, numbers, and special characters. Regularly remind users to update their passwords and discourage password sharing or reuse.
Monitoring and Auditing Role Activity using AWS CloudTrail:
Enable AWS CloudTrail to monitor and log events related to IAM roles. CloudTrail provides detailed information about actions taken by IAM roles, including who acted, when it occurred, and which resources were accessed. Regularly review CloudTrail logs to detect any unauthorized or suspicious activity. Configure alerts or integrate CloudTrail logs with a security information and event management (SIEM) system for real-time monitoring and proactive threat detection.
Implementing Least Privilege for Role Permissions:
Follow the principle of least privilege when defining role permissions. Only grant the minimum permissions necessary for the role to perform its intended tasks. Avoid granting broad permissions by default and instead, explicitly define specific actions and resources in IAM policies. Regularly review and fine-tune permissions to ensure they align with the actual requirements of the roles.
Utilizing IAM Conditions for Granular Access Control:
Leverage IAM conditions to add additional controls and constraints to role permissions. Conditions allow you to define rules based on factors such as time, IP address, and tag values. For example, you can restrict role access to specific IP ranges or enforce time-based access restrictions. Utilizing conditions enhances the granularity and control of IAM role permissions.
Conclusion
In this blog post, we explored the concept of IAM roles in AWS and their significance in access management. We discussed how IAM roles differ from other forms of access control, such as users and groups, and highlighted the benefits they offer, including least privilege access and reduced exposure of access credentials.
IAM roles play a crucial role in establishing secure and controlled access management within AWS environments. They ensure that entities have the necessary permissions to perform their tasks while adhering to the principle of least privilege. By leveraging IAM roles, organizations can enhance security, reduce the risk of unauthorized access, and achieve a more efficient and scalable access management framework.
In conclusion, we encourage readers to embrace IAM roles as a fundamental component of their AWS security strategy. By implementing IAM roles effectively, organizations can ensure secure access to AWS resources, simplify access management, and enhance the overall security posture of their AWS environments. Embrace IAM roles and unlock the full potential of secure and controlled access in the AWS cloud.
Remember, IAM roles are not just a best practice; they are a critical component in securing your AWS resources. Start leveraging IAM roles today and experience the benefits of granular access control and enhanced security in your AWS environment.
